Key Takeaways:
- Understand what a Cloud Access Security Broker (CASB) is and why it’s essential in cloud security.
- Learn about the various functions CASBs perform to secure cloud environments.
- Discover real-world examples illustrating the importance of CASBs in today’s cybersecurity landscape.
- Gain awareness of emerging trends and future developments in CASB technology.
Table of Contents:
- What Is A CASB?
- Critical Functions of a CASB
- CASBs and Compliance
- Emerging Trends and Future Developments
- Conclusion
What Is A CASB?
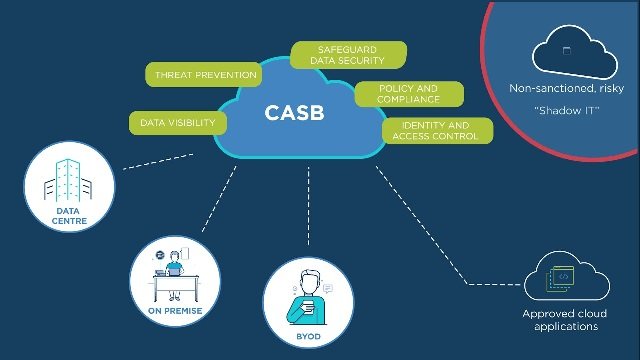
A Cloud Access Security Broker (CASB) acts as a gatekeeper, ensuring that corporate cloud services are secure and compliant. Positioned between cloud service users and providers, CASBoffer a robust layer of security in an increasingly cloud-based world. By controlling access to cloud assets and monitoring data exchanges, CASBs play a pivotal role in safeguarding against breaches and ensuring regulatory compliance. They mediate interactions between users and cloud services, offering a centralized point of control that addresses the security gaps intrinsic to cloud deployments. This centralized approach simplifies management and enhances the overall security posture by providing consistent policies and visibility across various cloud platforms.
The importance of CASBs has grown as organizations continue to embrace cloud technologies. Traditional security measures must often be revised for dynamic and distributed cloud environments. CASBs provide the tools to extend security controls beyond the corporate firewall, ensuring that data remains secure regardless of where it is stored or accessed. In essence, CASBs bridge the gap between on-premises infrastructure and cloud services, enabling organizations to fully leverage the benefits of cloud computing without compromising on security or compliance.
Critical Functions of a CASB
CASBs offer a range of capabilities to secure cloud environments. These include:
- Threat Protection: Identifying and mitigating risks before they reach the cloud. CASBs continuously monitor user activities and data flows to detect abnormal behaviors indicative of potential threats. Through advanced analytics and machine learning algorithms, CASBs can pinpoint suspicious activities that may go unnoticed, allowing quick intervention and remediation.
- Data Security: Ensuring that sensitive information remains confidential and unaltered. This involves encryption, tokenization, and other strategies to protect data at rest and in transit. Data security mechanisms within CASBs ensure that even if unauthorized access occurs, the data remains unintelligible and useless to potential attackers. Additionally, CASBs enforce data loss prevention (DLP) policies to prevent sensitive data from being shared or exfiltrated outside the organization’s approved channels.
- Compliance Assurance: Helping businesses adhere to regulations like GDPR or HIPAA. CASBs provide tools to automate compliance checks and generate necessary reports, making regulatory compliance more manageable. They support establishing and enforcing policies that align with specific compliance requirements, simplifying the audit process, and reducing the risk of non-compliance fines or penalties.
- Visibility and Control: Providing insights into cloud usage patterns and controlling access to cloud resources. CASBs offer comprehensive dashboards and reporting tools to help administrators understand who is accessing what, when, and how. This visibility helps identify misuse, unauthorized access, and potential data exfiltration, enabling timely responses to security incidents. By consolidating cloud security management into a single interface, CASBs simplify the monitoring and enforcing security policies across multiple cloud environments.
CASBs and Compliance
Compliance is a critical concern for organizations embracing cloud technology. CASBs aid in meeting regulatory requirements by offering visibility, control, and data security tools. For instance, cybersecurity compliance is becoming increasingly significant as regulatory landscapes evolve. By automating policy enforcement and providing detailed audit logs, CASBs make it easier for organizations to demonstrate compliance with industry standards and regulations.
Moreover, CASBs are crucial in maintaining compliance when dealing with cross-border data transfers and multi-jurisdictional regulations. They enable organizations to enforce geographic restrictions and ensure that data is processed and stored in compliance with local laws. This capability is precious for global enterprises that operate in multiple regions with varying regulatory requirements. By providing a unified approach to compliance management, CASBs reduce the complexity and administrative burden associated with regulatory compliance, allowing organizations to focus on their core business activities.
Emerging Trends and Future Developments
The CASB market is continually evolving. New features such as enhanced threat intelligence and machine learning algorithms are being integrated into CASBs. A recent article on cybersecurity trends highlights how these advancements are shaping the future of cloud security. As cyber threats become more sophisticated, CASBs incorporate AI-driven analytics to predict and mitigate threats more effectively, ensuring they remain at the forefront of cloud security solutions.
Machine learning techniques enable CASBs to adapt to new threat vectors and patterns dynamically, providing more proactive and resilient defense mechanisms that can better handle the intricacies of modern cyber-attacks. Additionally, integrating zero-trust principles and adaptive access controls within CASBs is revolutionizing how organizations approach cloud security. CASBs ensure that only authorized and legitimate users can access sensitive cloud resources by continuously verifying user identities and assessing the context of access requests.
Furthermore, the emergence of multi-cloud strategies has driven the need for CASBs to support seamless security management across different cloud platforms. As organizations increasingly adopt hybrid and multi-cloud environments, CASBs evolve to provide consistent security policies and controls, irrespective of the underlying cloud provider. This ensures that organizations can maintain a unified security posture while leveraging the strengths of various cloud services to meet their business needs.
Conclusion
As cloud adoption continues to rise, the role of CASBs in securing cloud environments becomes increasingly essential. These tools protect data, ensure compliance, and provide critical visibility into cloud usage, making them indispensable in modern cybersecurity frameworks. By integrating cutting-edge technologies and adapting to evolving threats, CASBs will continue to play a crucial role in safeguarding tomorrow’s cloud infrastructure. The continued evolution of CASB technology promises to deliver even more advanced security capabilities, ensuring that organizations can safely leverage the benefits of cloud computing without compromising on security or compliance.
In conclusion, CASBs are vital to any comprehensive cloud security strategy. Their ability to provide granular control, advanced threat protection, and robust compliance support makes them essential for organizations navigating the complexities of the cloud landscape. As cyber threats and regulatory requirements evolve, CASBs will remain at the forefront, enabling businesses to innovate securely and confidently in the digital era.